Tailscale, Mullvad, and More
Table of Contents

tldr; Tailscale allows you to create your own private, secure networks, like the LANs of yesteryear, and now they can have "exit nodes" that are Mullvad VPN servers.
I’ve been a Tailscale user for a while now, though my use waned as I struggled to deal with using a VPN as an exit node. For real, that was my problem. I really struggled with the exit nodes and VPNs. For a while I had a tailscale exit node, as simple Linux VM running in Digital Ocean, which is still an option because Tailscale can use any server as an exit node, but it was a pain to setup and manage and update…and, and, and…
Now Tailscale has a feature where you can use Mullvad VPN endpoints as exit nodes. This is got me right back into using Tailscale full time on all of my devices.
Check out the feature page here: https://tailscale.com/mullvad
NOTE: I have no affiliation with Tailscale or Mullvad. I’m a big fan of Tailscale because it is a CANADIAN 🇨🇦 company!

Also check out my other post about using Tailscale with Kubernetes.
Tailscale 🌐
As mentioned, Tailscale is a Canadian company that makes a VPN service that is very easy to use. But what is a VPN? Why have one at all? What are VPNs really good for? Do they work? There are still a lot of questions out there as to what a “virtual private network” really is. Is it just something we login to at work in most enterprises?
Tailscale makes creating software-defined networks easy: securely connecting users, services, and devices. - https://tailscale.com
Here’s the CEO talking about the VPN/Internet problem in the Tailscale blog:
We looked at a lot of options, and talked to a lot of people, and there was an underlying cause for all the problems. The Internet. Things used to be simple. Remember the LAN? But then we connected our LANs to the Internet, and there’s been more and more firewalls and attackers everywhere, and things have slowly been degrading ever since. - https://tailscale.com/blog/new-internet
I don’t want to get into the philosophical discussion here, but I think Tailscale is on to something, I’m just not exactly sure what it is…possibly something like how social networks may be changing into group chats. But that is for another blog post.
Mullvad 🦊
I have used PIA, Private Internet Access, for a long time. It’s a great VPN service. Mullvad is similar, but with a few key differences in that they are heavily privacy focused and have a unique way of “logging in”.
Prior to realizing that Tailscale could use Mullvad as an exit node, I had coincidentally been using Mullvad as my VPN for a month or so, wanting to try something new after my PIA subscription expired. It’s a bit more expensive, but the model is interesting in that you don’t have a subscription really, instead you pay $5 USD per month and you don’t have a username or password, only an account ID.
One thing to note is that Mullvad just doesn’t have the same wide Internet pipes as PIA does, though they do have servers in Canada. However, I don’t see that much of a difference in speed, though it is there. So that is something to consider if you are a heavy downloader.
Overall, a fascinating service that I need to learn more about.
Tailscale and Mullvad Together 🤝
Basically you enable Mullvad in Tailscale, it costs $5 USD per month for up to 5 devices. This 5 devices model is really useful, because that’s about what I have in terms of the number of devices that should be on Tailscale. Phones. Workstations. Laptops. Entertainment devices. Servers. Five devices is a good number for me, but if you need more, you just pay more.
First, enable Mullvad in Tailscale. Go to “Settings” and you can find it there.
After adding devices you should see something like the below.
NOTE: I’ve removed my devices from the list of course.
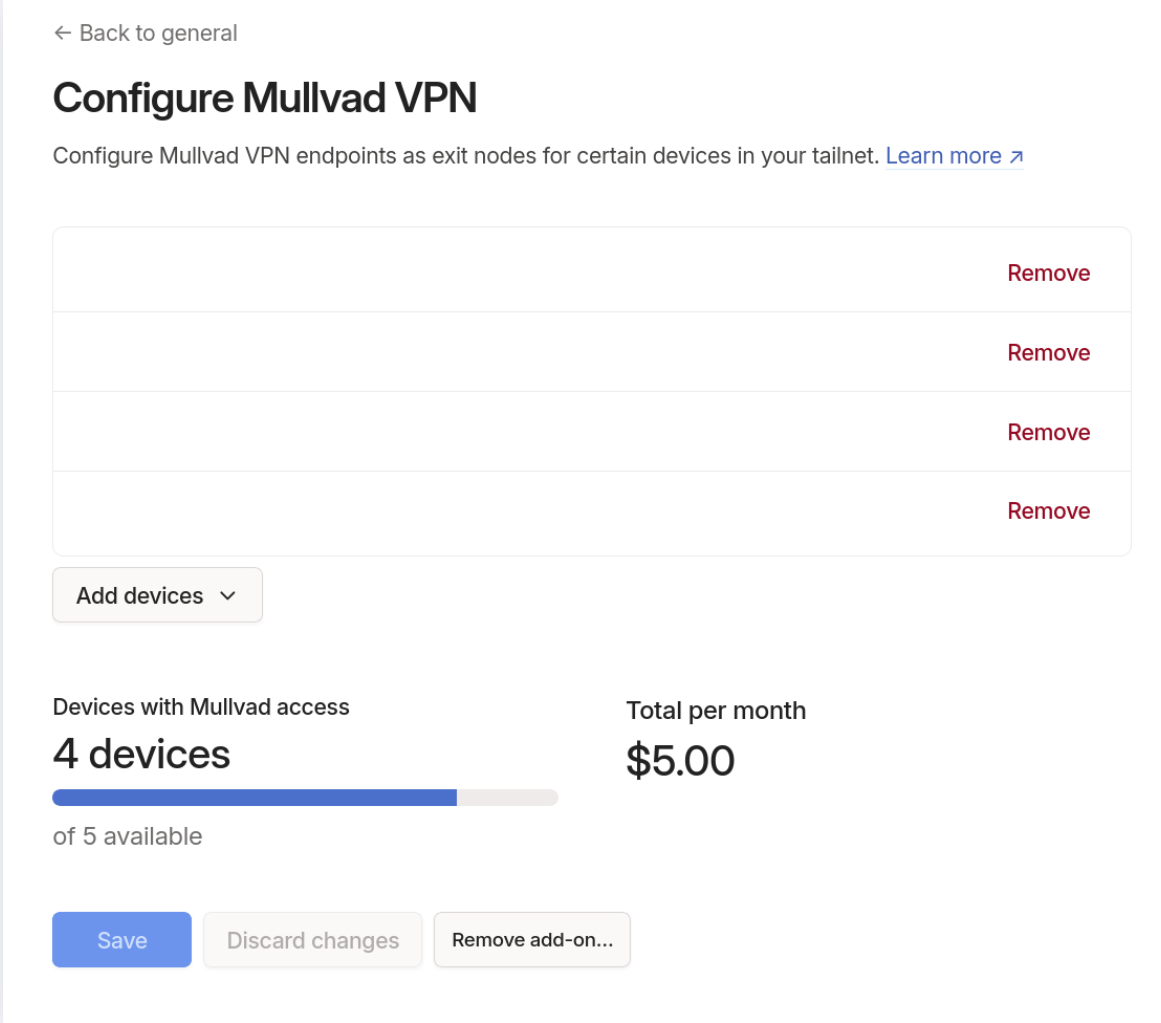
Once you enable Mullvad in Tailscale, you can select it as an exit node on your Tailscale devices. That’s it. No need to configure Tailscale, then configure Mullvad, then troubleshoot the inevitable configuration issues.
Using Mullvad as an Exit Node 🔄
If you want to see all the exit nodes:
$ tailscale exit-node list
IP HOSTNAME COUNTRY CITY STATUS
100.91.198.95 al-tia-wg-001.mullvad.ts.net Albania Tirana -
100.65.216.68 au-adl-wg-301.mullvad.ts.net Australia Any -
100.65.216.68 au-adl-wg-301.mullvad.ts.net Australia Adelaide -
100.70.240.117 au-bne-wg-301.mullvad.ts.net Australia Brisbane -
100.117.126.96 au-mel-wg-301.mullvad.ts.net Australia Melbourne -
100.88.22.25 au-per-wg-301.mullvad.ts.net Australia Perth -
100.100.169.122 au-syd-wg-001.mullvad.ts.net Australia Sydney -
100.79.65.118 at-vie-wg-001.mullvad.ts.net Austria Vienna -
100.120.7.76 be-bru-wg-101.mullvad.ts.net Belgium Brussels -
SNIP!
I use the just command runner to setup some easy commands to enable/disable Mullvad as an exit node.
tailscale-use-vpn:
sudo tailscale set \
--exit-node-allow-lan-access \
--exit-node=${MULLVAD_EXIT_NODE}
tailscale-no-vpn:
# blank exit node
sudo tailscale set --exit-node=
So if I need to I can turn off the VPN, for example Reddit blocks VPNs, not that I use Reddit, but it certainly comes up in Google searches.
Tailscale Access Control List 🔒
While Tailscale does talk about being easy to use, it also has complex looking ACLs. I hadn’t used the ACLs previously, but now with more devices on Tailscale, I wanted to control what could access what, specifically I wanted a couple of devices only to be able to use the exit nodes, not access any other devices on the tailnet.
I struggled a bit with the ACLs, as any kind of RBAC is challenging to get right, but I had three main realizations that allowed me to get the right setup.
1. The only action is “accept”…this rattled my cage for a bit, as I was expecting deny or some other keywords.
Tailscale access rules deny access by default. As a result, the only possible action is accept. accept allows traffic from the source (src) to the destination (dst). - docs
2. Users: You can control based on what user the device is logged in as on the tailnet. I didn’t realize this initially and was just trying to configure by device. And then realizing my mistake, it was much easier, as my main devices are logged in as me, and the other Internet/VPN only devices have their own users that were invited to the tailnet. Duh!
3. Groups: There is an “autogroup” for accessing the Internet which means you can set users to only have access to the Internet, and not any other devices on the tailnet. Perfect!
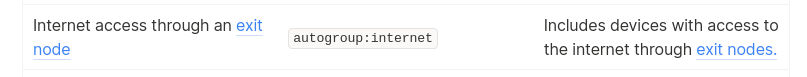
In the end my ACLs were maybe 10 lines of text, but it took a while to get there.
Conclusion 🎯
I’m really happy to be back to using Tailscale full time. We all really need to have better operational security for our Internet, phones, and application use…which I may be violating by even mentioning my use of Tailscale and Mullvad. But I think it’s a good thing to be talking about, and I hope to see more people using better tools to secure their Internet access.




